Cybersecurity
Strengthening Your Digital Fortress: A Comprehensive Guide to Cybersecurity
Last Updated
2023/07/06

Introduction: In today’s interconnected world, where digital technology is deeply integrated into our daily lives, the importance of cybersecurity cannot be overstated. Cyber threats continue to evolve, posing significant risks to individuals, businesses, and even nations. Therefore, it is crucial to stay vigilant and implement effective cybersecurity measures to safeguard sensitive information and maintain digital trust. This blog post aims to provide you with a comprehensive guide to cybersecurity, equipping you with the knowledge and tools to fortify your digital fortress.
- Understanding Cybersecurity: Before diving into specific security practices, it is important to grasp the fundamental concepts of cybersecurity. Explore the various types of cyber threats, such as malware, phishing, ransomware, and social engineering. Gain insight into the motivations of hackers and their techniques, allowing you to better anticipate and mitigate potential attacks.
- Strengthening Passwords and Authentication: One of the simplest yet most effective ways to enhance your cybersecurity is by adopting strong passwords and multi-factor authentication (MFA). Discover strategies for creating robust passwords, including length, complexity, and uniqueness. Learn how MFA adds an extra layer of protection by requiring multiple forms of authentication, such as passwords, biometrics, or security tokens.
- Securing Your Home Network: As our homes become more connected, it is essential to secure our Wi-Fi networks. Explore the steps to protect your home network from unauthorized access. This includes changing default router passwords, implementing network encryption (WPA2/WPA3), enabling firewalls, and regularly updating firmware.
- Safeguarding Personal and Financial Data: Personal and financial data are prime targets for cybercriminals. Uncover best practices for protecting sensitive information, such as credit card details, Social Security numbers, and personal identification. Explore encryption techniques, secure online transactions, and strategies for safely managing and disposing of data.
- Awareness of Social Engineering Attacks: Social engineering attacks exploit human psychology rather than technical vulnerabilities. Educate yourself about different types of social engineering techniques, such as phishing emails, phone scams, and pretexting. Learn how to recognize and respond to these threats effectively to avoid falling victim to social engineering attacks.
- Regular Software Updates and Patching: Software vulnerabilities often provide an entry point for cyber attackers. Discover the importance of regular software updates and patching to address known security vulnerabilities. Explore different methods for keeping your operating systems, applications, and devices up to date, ensuring that you have the latest security patches.
- Backing Up Your Data: Data loss due to cyber incidents or hardware failures can be devastating. Implement a robust backup strategy to protect your valuable data. Learn about different backup methods, such as cloud storage and offline backups, and establish a routine for regular backups. Additionally, understand the importance of testing your backups to ensure their reliability.
- Educating Yourself and Your Organization: Cybersecurity is a shared responsibility, and education is key to building a strong security culture. Stay updated on the latest threats and trends by following reputable sources. Encourage cybersecurity awareness within your organization or community through training programs and simulated phishing exercises. Promote a culture of reporting and accountability to address security incidents promptly.
- Securing Mobile Devices: Mobile devices have become indispensable in our lives, but they also present unique security challenges. Explore best practices for securing smartphones and tablets, including setting strong device passcodes, enabling device encryption, and being cautious with app downloads and permissions. Additionally, consider using mobile security solutions for added protection.
- Seeking Professional Help: In complex cybersecurity scenarios, it may be necessary to consult professionals or security firms for assistance. Understand when to reach out to experts, such as incident response teams or ethical hackers, to assess vulnerabilities and recommend appropriate remediation strategies.
Conclusion: Cybersecurity isa critical aspect of our digital lives, and investing time and effort in fortifying our defenses is essential. By implementing the practices discussed in this comprehensive guide, you can significantly reduce the risk of falling victim to cyber threats. Remember, cybersecurity is an ongoing process that requires continuous education, awareness, and adaptation to stay ahead of evolving threats. By prioritizing cybersecurity and taking proactive measures to protect your digital assets, you can create a safer online environment for yourself, your organization, and your community. Stay informed, stay vigilant, and stay secure!
Related Posts
Get Latest Technologies, Development Tips, & Trending Solutions.

Building a Cybersecurity Culture: Empowering Employees to Defend Against Cyber Threats
Introduction:In today’s digital age, cybersecurity is a shared responsibility that extends beyond the IT department. Employees play a crucial role in defending against cyber threats and protecting sensitive information. To establish a strong cybersecurity posture, organizations must foster a cybersecurity culture that empowers employees to be proactive and vigilant. This blog post explores the importance […]

The Rise of Ransomware: Protecting Your Data in an Evolving Threat Landscape
Introduction:Ransomware attacks have emerged as one of the most devastating and prevalent cyber threats in recent years. These malicious attacks encrypt your data and demand a ransom for its release, causing significant financial and operational damage to individuals and organizations alike. This blog post delves into the rise of ransomware and provides essential strategies to […]
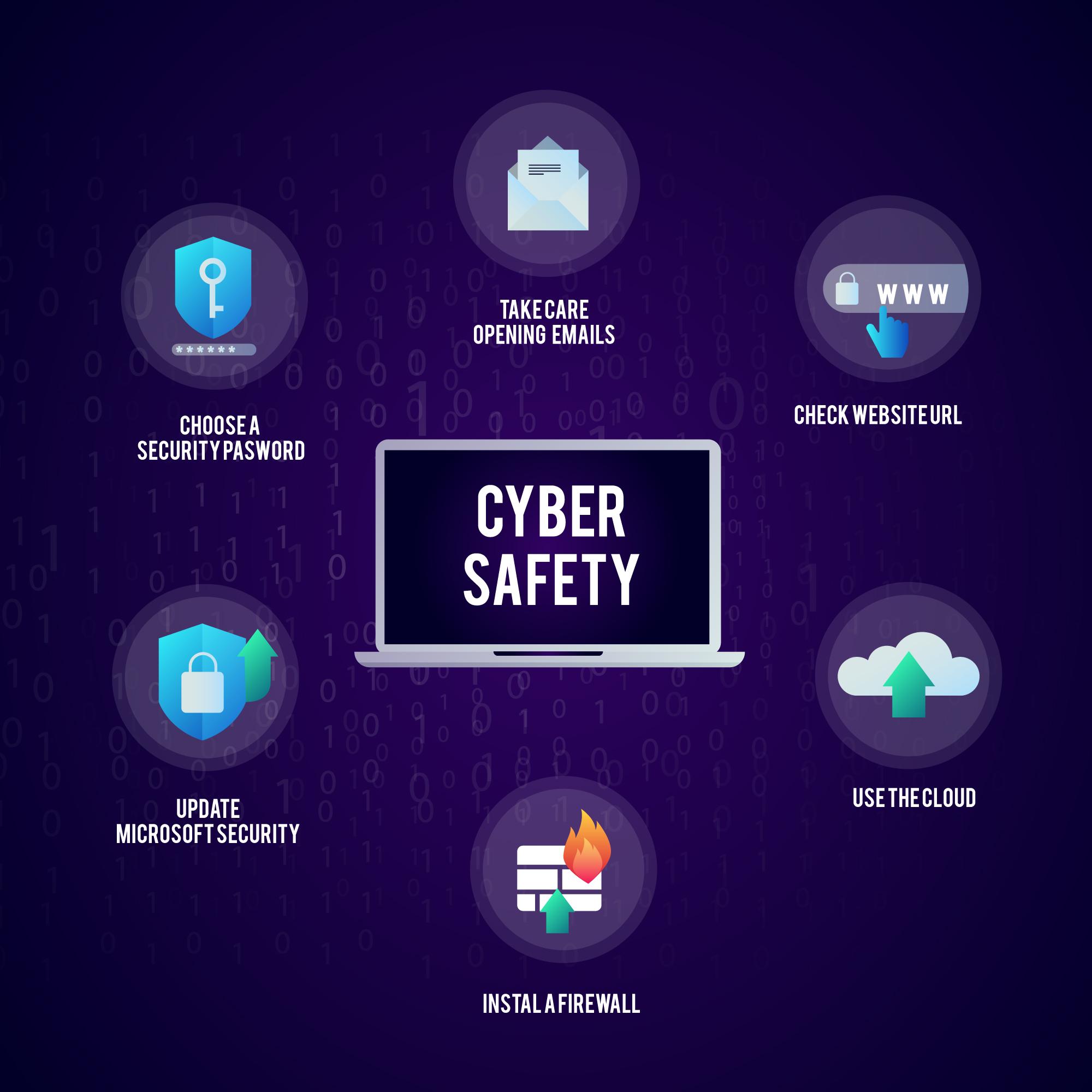
10 Essential Cybersecurity Practices to Safeguard Your Digital World
Introduction:In an increasingly interconnected and digital landscape, the need for robust cybersecurity measures has become paramount. Cyber threats pose significant risks to individuals, businesses, and organizations of all sizes. This blog post aims to provide you with 10 essential cybersecurity practices that will help you safeguard your digital world. By implementing these practices, you can […]