Cybersecurity
10 Essential Cybersecurity Practices to Safeguard Your Digital World
Last Updated
2023/07/06
Introduction:
In an increasingly interconnected and digital landscape, the need for robust cybersecurity measures has become paramount. Cyber threats pose significant risks to individuals, businesses, and organizations of all sizes. This blog post aims to provide you with 10 essential cybersecurity practices that will help you safeguard your digital world. By implementing these practices, you can enhance your online security, protect sensitive information, and mitigate the risk of falling victim to cyber attacks.
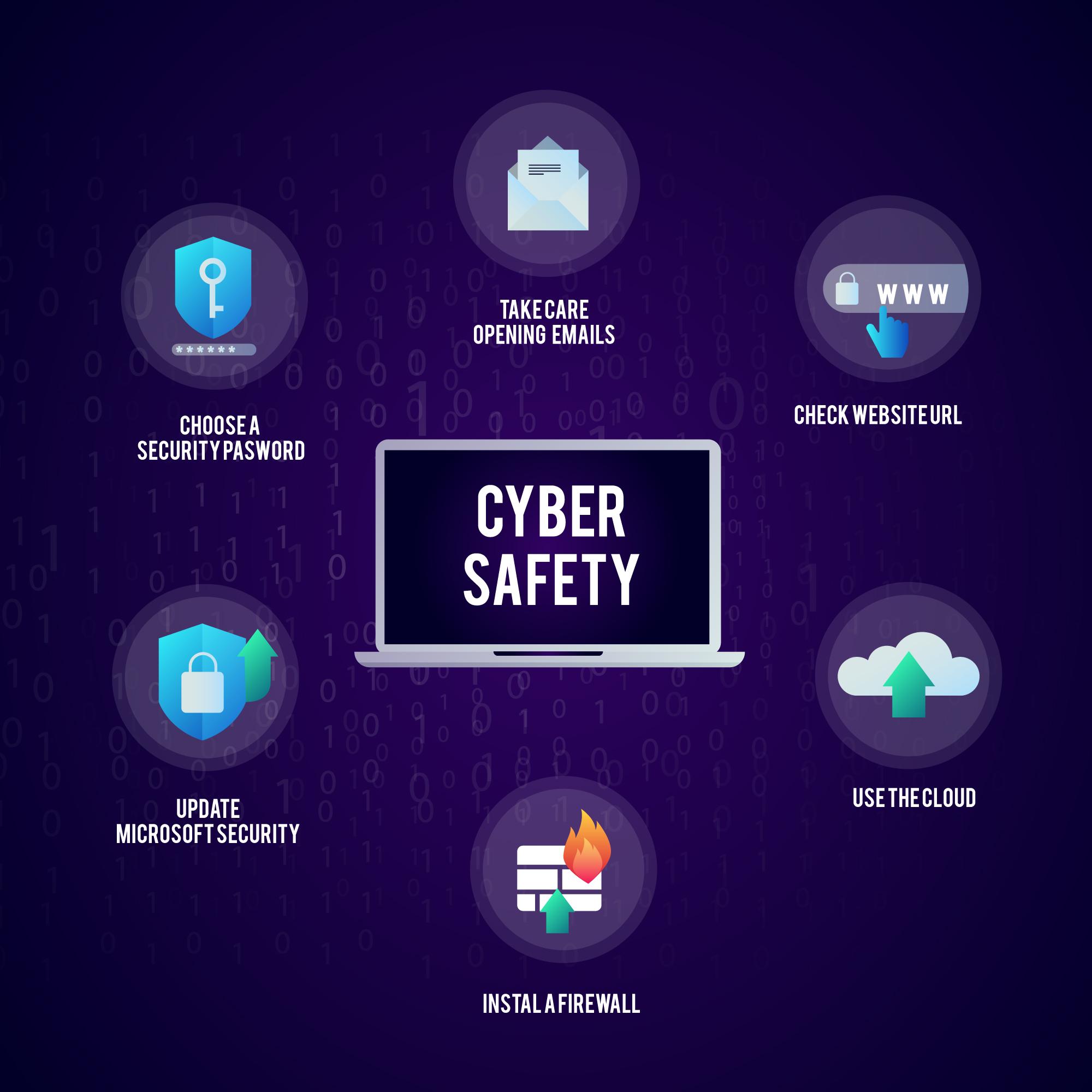
- Strong Passwords and Multi-Factor Authentication (MFA):
Create strong, unique passwords that are difficult to guess. Incorporate a combination of upper and lowercase letters, numbers, and special characters. Implement MFA whenever possible to add an extra layer of protection by requiring multiple forms of authentication, such as codes sent to your mobile device or biometric scans. - Keep Software and Operating Systems Up to Date:
Regularly update your software, applications, and operating systems. Software updates often include security patches that address known vulnerabilities, helping to prevent potential exploits by cybercriminals. Enable automatic updates or set reminders to ensure you stay current. - Phishing Awareness and Email Security:
Be vigilant against phishing attacks, where cybercriminals impersonate legitimate entities to trick you into revealing sensitive information. Avoid clicking on suspicious links or downloading attachments from unknown sources. Enable spam filters and use email security tools to minimize the risk of phishing emails reaching your inbox. - Secure Wi-Fi Networks:
Secure your home and office Wi-Fi networks by changing default router passwords, using strong encryption protocols (WPA2/WPA3), and hiding your network’s SSID. Additionally, consider implementing a separate guest network for visitors to isolate their access from your main network. - Regular Data Backups:
Implement a comprehensive backup strategy to protect your valuable data from loss or ransomware attacks. Regularly back up your files and store them in secure locations, such as external hard drives or cloud storage services. Test your backups periodically to ensure they can be successfully restored. - Install Antivirus and Anti-Malware Software:
Deploy reputable antivirus and anti-malware software on all your devices. These tools help detect and remove malicious software, providing an essential layer of defense against a wide range of cyber threats. Keep the software updated to ensure it can effectively identify and neutralize new threats. - Use a Virtual Private Network (VPN) for Secure Internet Connections:
When connecting to public Wi-Fi networks or accessing sensitive information online, use a VPN to encrypt your internet traffic and protect your data from potential eavesdropping. A VPN creates a secure tunnel between your device and the internet, ensuring privacy and anonymity. - Employee Training and Security Awareness:
Educate your employees about cybersecurity best practices, emphasizing the importance of strong passwords, safe browsing habits, and recognizing potential threats like phishing attempts. Conduct regular training sessions and keep your workforce updated on the latest cyber threats and preventive measures. - Regular Security Assessments and Penetration Testing:
Periodically conduct security assessments and penetration tests to identify vulnerabilities in your systems and networks. Engage with cybersecurity professionals who can simulate real-world attacks to uncover weaknesses and provide recommendations for strengthening your defenses. - Create an Incident Response Plan:
Prepare an incident response plan that outlines the steps to be taken in the event of a cyber attack or security breach. Assign roles and responsibilities to relevant team members, establish communication protocols, and document the necessary actions to minimize damage, contain the incident, and restore normal operations swiftly.
Conclusion:
Cybersecurity is a critical component of our digital lives. By implementing these 10 essential cybersecurity practices, you can significantly reduce the risk of falling victim to cyber attacks. Stay proactive, stay informed, and continually adapt your security measures to counter evolving threats. Protecting your digital world is an ongoing
Related Posts
Get Latest Technologies, Development Tips, & Trending Solutions.

Building a Cybersecurity Culture: Empowering Employees to Defend Against Cyber Threats
Introduction:In today’s digital age, cybersecurity is a shared responsibility that extends beyond the IT department. Employees play a crucial role in defending against cyber threats and protecting sensitive information. To establish a strong cybersecurity posture, organizations must foster a cybersecurity culture that empowers employees to be proactive and vigilant. This blog post explores the importance […]

The Rise of Ransomware: Protecting Your Data in an Evolving Threat Landscape
Introduction:Ransomware attacks have emerged as one of the most devastating and prevalent cyber threats in recent years. These malicious attacks encrypt your data and demand a ransom for its release, causing significant financial and operational damage to individuals and organizations alike. This blog post delves into the rise of ransomware and provides essential strategies to […]

Strengthening Your Digital Fortress: A Comprehensive Guide to Cybersecurity
Introduction: In today’s interconnected world, where digital technology is deeply integrated into our daily lives, the importance of cybersecurity cannot be overstated. Cyber threats continue to evolve, posing significant risks to individuals, businesses, and even nations. Therefore, it is crucial to stay vigilant and implement effective cybersecurity measures to safeguard sensitive information and maintain digital […]